最近生产服务器OpenSSH版本较低存在安全漏洞,所以需要升级OpenSSH版本。由于是SSH远程连接升级为了以防万一需要telnet远程连接方式备用,所以先研究telnet怎么进行远程连接。
安装 telnet telnet-server xinetd
-
在线安装
直接执行在线安装命令即可
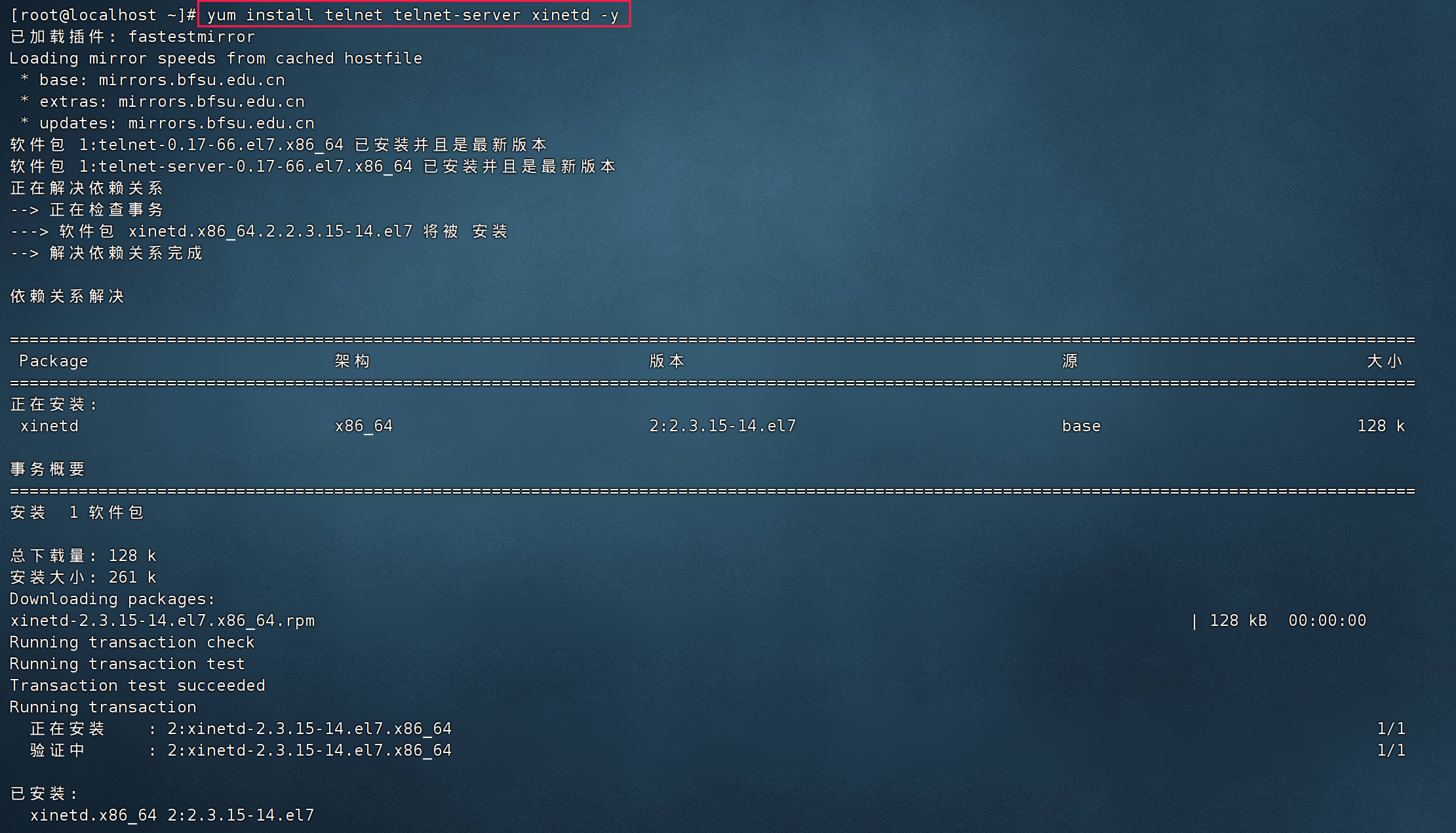
yum install telnet telnet-server xinetd -y
-
离线安装
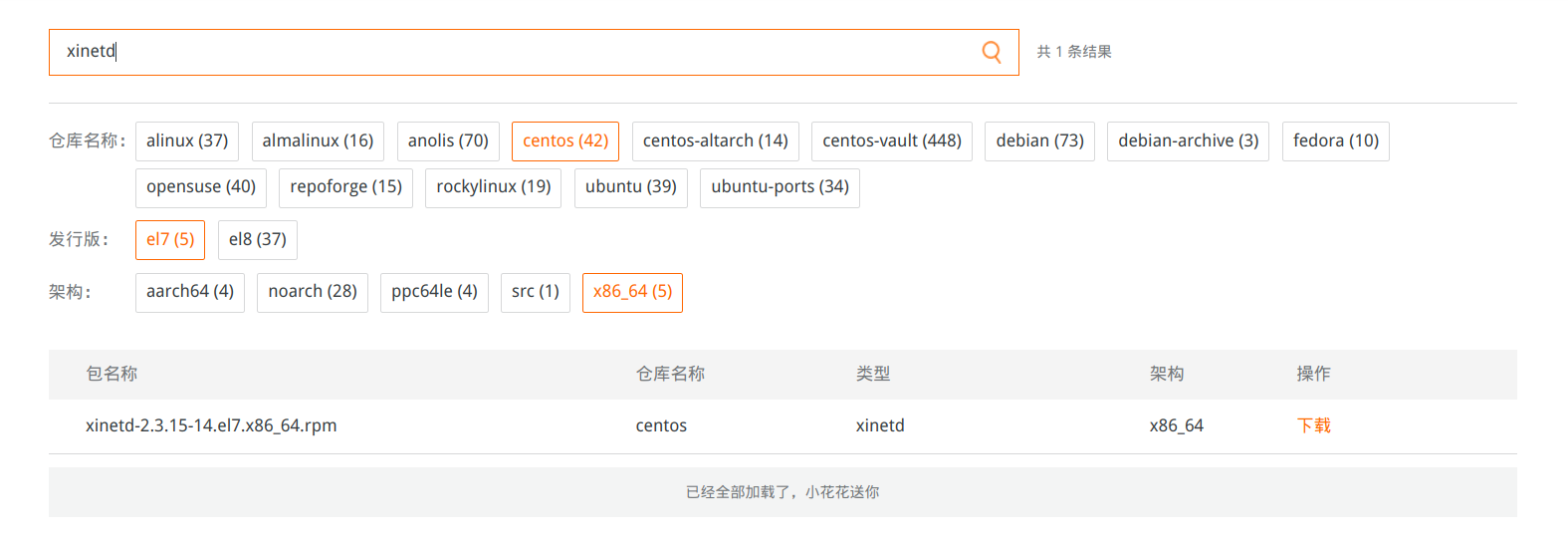
下载rpm安装包,离线包下载地址:https://developer.aliyun.com/packageSearch 自行搜索并下载(注意选择版本和架构等)
设置启动telnet服务
启动服务并设置自启动(systemctl start启动,systemctl status查看启动状态,systemctl enable允许自启动)
systemctl start telnet.socket
systemctl start xinetd
systemctl status telnet.socket
systemctl status xinetd
systemctl enable telnet.socket
systemctl enable xinetd

开放端口
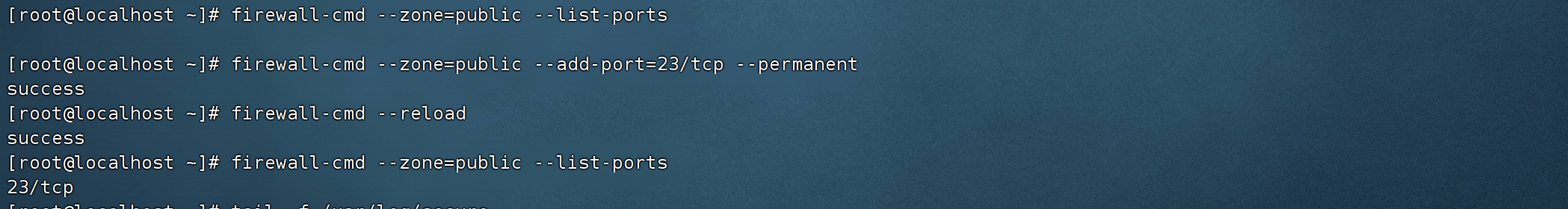
打开23端口,firewall-cmd --zone=public --add-port=23/tcp --permanent 打开23端,firewall-cmd --reload 重载设置,firewall-cmd --zone=public --list-ports 查看打开的端口列表
firewall-cmd --zone=public --add-port=23/tcp --permanent
firewall-cmd --reload
firewall-cmd --zone=public --list-ports
客户端(本地)连接
客户端需要支持telnet(安装telnet,linux: yum install telnet -y;windows打开服务)
javalx@javalx-PC:~$ telnet 192.168.18.80
Trying 192.168.18.80...
Connected to 192.168.18.80.
Escape character is '^]'.
Kernel 3.10.0-1160.el7.x86_64 on an x86_64
localhost login: root
Password:
Login incorrect
登录错误:查看服务端的日志 tail -f /var/log/secure,发现终端的远程连接被拦截了,添加终端允许并重启服务即可(编辑/etc/securetty末行追加pts/2)
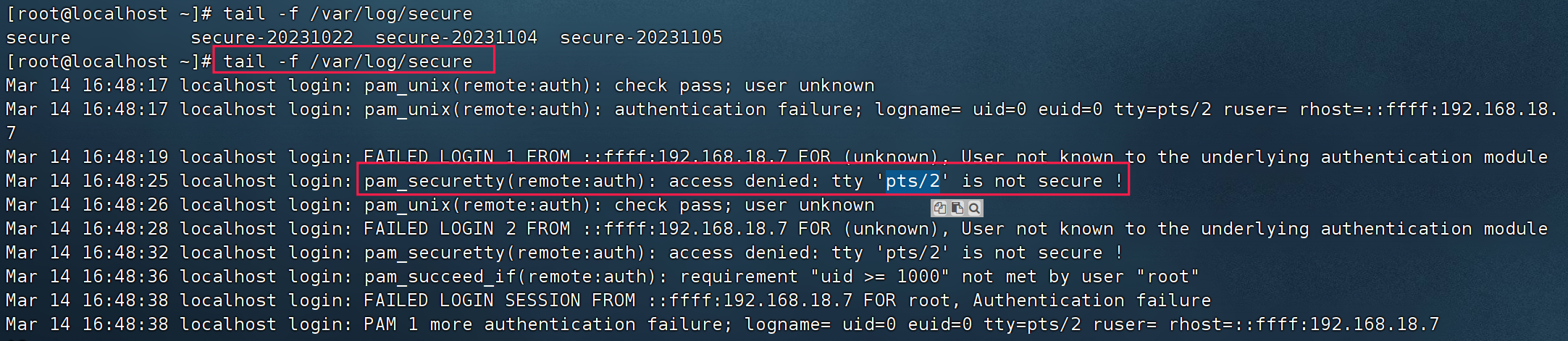
// echo 'pts/2' >>/etc/securetty 功效同下面的编辑追加
[root@localhost ~]# vi /etc/securetty
[root@localhost ~]# systemctl restart telnet.socket
[root@localhost ~]# systemctl restart xinetd

重新在客户端连接:
javalx@javalx-PC:~$ telnet 192.168.18.80
Trying 192.168.18.80...
Connected to 192.168.18.80.
Escape character is '^]'.
Kernel 3.10.0-1160.el7.x86_64 on an x86_64
localhost login: root
Password:
Last failed login: Thu Mar 14 16:48:38 CST 2024 from ::ffff:192.168.18.7 on pts/2
There was 1 failed login attempt since the last successful login.
Last login: Thu Mar 14 16:42:55 from 192.168.18.7
[root@localhost ~]# ^C
[root@localhost ~]# pwd
/root
[root@localhost ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 52:54:00:d1:67:6c brd ff:ff:ff:ff:ff:ff
inet 192.168.18.80/24 brd 192.168.18.255 scope global noprefixroute ens3
valid_lft forever preferred_lft forever
inet6 2408:8210:3c50:4e60:5054:ff:fed1:676c/64 scope global mngtmpaddr dynamic
valid_lft 230627sec preferred_lft 144227sec
inet6 fe80::5054:ff:fed1:676c/64 scope link
valid_lft forever preferred_lft forever
[root@localhost ~]#


评论区